Adobe Acknowledges Flaw in PDF for Windows, Urges Registry Hacks
Confirming a statement made by Petko D. Petkov on his GNUcitizen.org blog over two weeks ago, almost in passing, Adobe has released a security advisory warning of a potential exploitable flaw in its Acrobat and Adobe Reader software. While Petkov has never made the exploit itself public, Adobe's suggested system registry fix suggests a maliciously crafted PDF can be made to send e-mail undetected.
Instructions posted to Adobe's security site tell Acrobat and Adobe Reader users where they should edit a particular entry in the Windows System Registry. That entry contains a list of protocol identifier stubs that PDF files may typically find embedded. There, users will find a long string terminated by zero (REG_SZ), which lists several URI stubs followed by digits evidently denoting how the PDF handler should process them.
As the instructions state, changing the digit attributed to mailto: from 2 to 3 disables processing of URLs embedded in a PDF file that contain mailing links, while deleting that portion of the entry altogether forces Acrobat to show a prompt asking the reader what to do with the link. Whether this latter option disables a PDF document from sending a specific e-mail without the user's permission is unclear.
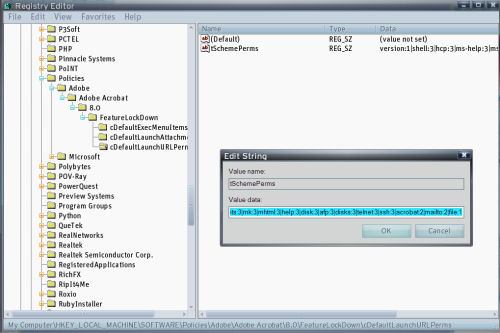
The figure above shows Registry Editor being used to edit the Windows System Registry as suggested by Adobe. The company said it plans to issue a permanent fix for this problem as an engineering update before the end of October. In the meantime, it's advising Windows customers to edit their registry manually - which, as any system admin knows, is a dangerous proposition.
Though Adobe did not say so explicitly, the fact that the problem Petkov discovered can be thwarted by disabling handling of the mailto: resource identifier, clearly suggests PDFs can send mail in the background without user intervention.
What's unknown at this time is whether a specific e-mail client must be relied upon for such stealth functionality to work. In other words, does Microsoft Outlook pass the mail through undetected, or does Outlook or any specific client play a role here?
Unusually, Petkov himself has posted no public comment about Adobe's acknowledgement today, though Adobe does credit him with the discovery of the vulnerability.
