Don't wait for Microsoft's patch: Secure Windows now from Monday's 0-day
There's an old ActiveX control hanging around many Windows systems that's still accessible to Internet Explorer, whose original purpose was to tune into MPEG2 transport streams -- typically live video streams sent from a server using MPEG2 format. Yes, MPEG2 transport streams still exist, but any more, browsers including IE8 have appropriate plug-ins to handle them -- Windows Media Player is one, Apple's QuickTime is another.
But still there's this ActiveX control sitting there doing nothing, waiting to be leveraged for an attack. Earlier today, Microsoft acknowledged a SANS Internet Storm Center report saying that there's an active exploit of this disused bit of functionality published on Chinese Web sites. Apparently malicious users are utilizing it now in "drive-by" attacks that could result, say security experts including Sophos' Graham Cluley, in installation and execution of nearly any malicious payload.
This morning, Microsoft security engineer Chengyun Chu noted that in order for a Web site to use this exploit to deliver this payload, the user would need to click on a link that launches that Web site. That makes Outlook relatively safe if that link is embedded in the type of e-mail message that says, "Check this out!" just so long as the user doesn't click on that link. In other words, the code cannot be triggered automatically through Microsoft's e-mail client.
While Cluley and others are chiding Microsoft for not coming up with a patch, the sad fact is, it actually might not need to. In this morning's security advisory, the company admitted right up front that its current set of engineers have forgotten what this ActiveX control was ever needed for: "Our investigation has shown that there are no by-design uses for this ActiveX Control in Internet Explorer which includes all of the Class Identifiers within the msvidctl.dll that hosts this ActiveX Control," the security advisory reads. "For Windows XP and Windows Server 2003 customers, Microsoft is recommending removing support for this ActiveX Control within Internet Explorer."
In the meantime, the company is recommending that users remove support for this control themselves. It's an easy process for anyone who's ever used REGEDIT before, although it's just a little arduous -- there are as many as 45 possible CLSID numbers for this single control (which shows you how ridiculous the ActiveX control management process was in its heyday). The security advisory lists them all, although you do not need to go through Microsoft's advised steps of cutting and pasting them all individually into Notepad (talk about making something more difficult than it has to be!).
Instead, you can use our much simpler method of making certain your Windows installation is safe by doing the following:
1. Open Security Advisory 972890 and scroll down to General Information. Open the Suggested Actions tier, followed by Workarounds, and scroll down until you see the long list marked Class Identifier.
2. Start the Windows Registry Editor (REGEDIT). (For Vista, you may need to click on Continue at the UAC prompt.)
3. In the left pane, open the folder corresponding to the Registry tier \HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\ActiveX Compatibility. The good news here is that all the CLSIDs in this segment of the Registry, and all the CLSIDs in Microsoft's warning list, are in hexadecimal numerical order, so you won't have to search each one from top to bottom.
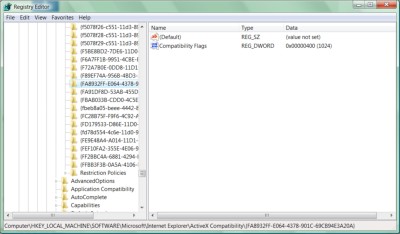 4. Scan the Registry to see if any of the CLSIDs correspond exactly to any of the 45 Registry items flagged by Microsoft. More than one may correspond. If none correspond, you are already safe from this exploit. Betanews was unable, for example, to find any of the 45 Registry entries on our Windows XP or Vista systems, and we don't expect to see it in Windows 7.
4. Scan the Registry to see if any of the CLSIDs correspond exactly to any of the 45 Registry items flagged by Microsoft. More than one may correspond. If none correspond, you are already safe from this exploit. Betanews was unable, for example, to find any of the 45 Registry entries on our Windows XP or Vista systems, and we don't expect to see it in Windows 7.
5. If you do find an offending CLSID, then do not delete it. That actually won't change anything at all, believe it or not. Instead, choose its entry from the left pane.
6. Check the right pane for a value named Compatibility Flags. If it does not yet exist, you'll need to create it. Right-click on the empty space in the right pane, and from the popup menu, select New, Binary Value. A new listing will be created that moment, which you'll need to rename. Type Compatibility Flags and Enter.
7. Right-click on Compatibility Flags and from the popup menu, select Modify. In the Edit DWORD Value dialog box, under Value data, type 400, leave the Base setting on Hexadecimal, then click on OK. Repeat this process for all the remaining CLSIDs in Microsoft's list.
What this does is set the kill bit for the control. It's still registered (and it's still taking up space on your hard drive, doing nothing), but now it's at least turned off, so it can't be leveraged in an attack.
