Has Firefox 3 certificate handling become too 'scary?'
In a scenario reminiscent of the fairy tale about the fellow who cries "wolf" too often, security engineers are actively wondering whether Firefox' "blowing of the whistle" on self-signed certificates is a) frightening, and b) fair to developers.
One of the oft-touted improvements in Mozilla's Firefox 3.0 Web browser has been its improved handling for sites that authenticate their own identities using SSL certificates -- the kind used to initiate encrypted transactions with HTTPS protocol. For instance, a site whose authentication is verified will be indicated in Firefox's address bar by having its icon expanded to a full name, printed on a green background. Supposedly, this is to reassure the user that everything's copacetic.
But on the other end of the scale is the browser's handling of certificates it cannot validate, which in recent weeks, multiple users and developers alike have characterized with the word "scary." Now, Firefox replaces the Web page with a full-screen warning, featuring a traffic-cop pictogram and explaining the problem in detail. The color scheme is yellow, not red (which Firefox reserves for such things as suspected phishing sites or scam practitioners). Still, developers are asking whether the level of alarms Firefox raises now are so intense that many users will actually choose to ignore them rather than pay attention to them.
The issue may have become critically important earlier this year, when a major potential Internet-wide exploit was uncovered by security researcher Dan Kaminsky. As security software provider Qualys' Chief Technical Officer Wolfgang Kandek told BetaNews in an interview last month, the success of spoofs that involved that exploit may have come down to whether Web browser users actually read the warnings that tell them the SSL certificates they've received don't match or can't be validated.
In order for you, the everyday user, to avoid falling into the trap yourself, Kandek told us, "you would depend on a browser popping up saying a certificate does not match. The question would be, how many people understand that? How many people simply do not acknowledge that? What happens every once in a while is that [a certificate] expires, or there is a redirect. I get these messages every once in a while, I usually read them, and then decide, can I go on or not? Of course, a common person would [have trouble with] that because you have to be reasonably security-savvy to understand the warning message and decide what to do."
Mozilla began implementing a stricter policy on warning its users, according to its developers' site, after having received no fewer than three independently created warnings about how, at that time, Firefox 2 handled so-called self-signed certificates (SSC). These are valid, though not authenticated, certificates that can be used for encrypting connections, as long as the user is willing to trust their validity in the absence of a third party certificate authority (CA) -- such as VeriSign -- that can do the validation on the user's behalf.
The warning, essentially, stated that the earlier method's handling of SSCs gave users a kind of a plea to become accepted. Once it was, its acceptance extended to any so-called alternate site names the certificate may contain, even though those alternate names weren't presented to the user. Conceivably, an SSC could be used as a kind of gadget for maneuvering invalid Web sites into becoming validated automatically, leveraging the user's willingness to just trust the main site for what it says it is, and get on with it.
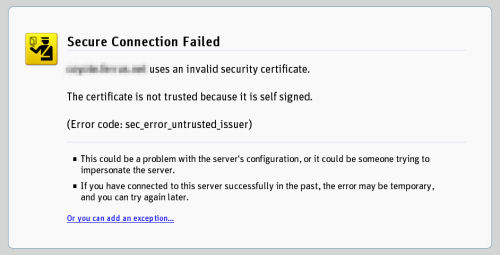
Developers often build SSCs for themselves. It's an easy process, especially if you have Internet Information Services 7.0; and both Microsoft Internet Explorer 7 and Firefox (versions 3.0 and above, as well as version 2.0.0.15), in fairness, have tightened their behavior with regard to recognizing a self-signed certificate that a CA can't vouch for.
Sometimes it makes sense for a Web developer to create SSCs from a security standpoint -- for instance, it may not be a good idea to register on the books of a third party, the name, IP, and DNS addresses for a project operating in stealth. Otherwise, SSCs are often just more convenient for developers than having to register, and then pay for, every certificate for every project.
Meanwhile, SSCs and expired certificates turn up in the most unusual places, including such places as Google Checkout, Yahoo's publisher network, and LinkedIn, according to the SSL developers' blog SSL Shopper.
So Firefox's sudden treatment of SSCs as "second-class citizens" -- or, in a sense, as more prone to suspicion than a standard HTTP site with no encryption at all -- is annoying many independent developers, including open source advocates, some of whom go so far as to question whether they should be paying for authentication.
In a personal blog post three weeks ago, developer Nat Tuck wrote, "Mozilla Firefox 3 limits usable encrypted (SSL) web sites to those who are willing to pay money to one of their approved digital certificate vendors. This policy is bad for the Web. Not only does it make users less secure overall by reducing the number of encrypted connections, it damages the basic principle of equality among Web participants."
In a blog post two weeks ago intended to put the entire issue to rest, Mozilla developer Jonathan Nightingale responded to this claim and others by saying Firefox 2's warnings were easier for users to ignore or just blindly accept, and that a real security issue could emerge from that acceptance.
"With a self-signed certificate, we don't know whether to trust it or not," Nightingale wrote. "It's not that these certificates are implicitly evil, it's that they are implicitly untrusted -- no one has vouched for them, so we ask the user. There is language in the dialogs that talks about how legitimate banks and other public web sites shouldn't use them, because it is in precisely those cases that we want novice users to feel some trepidation, and exercise some caution. There is a real possibility there, hopefully slim, that they are being attacked, and there is no other way for us to know."
As for developers who sign their own certificates for their own purposes, he goes on, well, they know who they are, and certainly it's up to them whether they trust themselves or not. But the new warning is meant to wake people up, and give them an opportunity to override Firefox's default behavior -- which is now to distrust -- with a statement of trust that is applied specifically to the main site under suspicion.
One alternative to the use of SSLs that many developers may not be aware of comes from a company called StartCom, which offers some Class 1 digital certificates for free.