Microsoft and Mozilla leave Web users tangled over 'variant' vulnerability
 In what is now indisputably the most important vulnerability addressed during last Tuesday's record round of Windows patches, the two companies most affected by the problem -- Microsoft and, to a lesser extent, Mozilla -- could not help but be caught in a tangle of miscommunication exacerbated to a large extent by overhype from a sea of blogs. As a result, it's everyday users who are left confused and bewildered, even though no known exploit for the vulnerability exists.
In what is now indisputably the most important vulnerability addressed during last Tuesday's record round of Windows patches, the two companies most affected by the problem -- Microsoft and, to a lesser extent, Mozilla -- could not help but be caught in a tangle of miscommunication exacerbated to a large extent by overhype from a sea of blogs. As a result, it's everyday users who are left confused and bewildered, even though no known exploit for the vulnerability exists.
The problem involves both the ".NET Framework Assistant" add-on and "Windows Presentation Manager" plug-in made by Microsoft for Mozilla Firefox, both of which are installed automatically -- and without warning -- by Microsoft's .NET Framework 3.5 Service Pack 1. One of Microsoft's patches last week, as explained in a Microsoft bulletin, addresses the functionality of 3.5 SP1 that's made available through these Firefox extensions.
Meanwhile, on its end, Mozilla opted to disable these extensions at the browser level, for reasons explained by its vice president of engineering, Mike Shaver, as, "because of the difficulties some users have had entirely removing the add-on, and because of the severity of the risk it represents if not disabled." The move was made only after having contacted Microsoft first; and Microsoft agreed with the decision, Shaver said.
This contradicts a multitude of reports over the weekend saying that Mozilla had taken action in defiance of Microsoft's extensions.
But this morning, Microsoft issued a clarification to Mozilla, apparently correcting its own misunderstanding of the matter (or rather, when the weekday crew came in to relieve the weekend crew): The extensions themselves actually have nothing whatsoever to do with the Patch Tuesday vulnerability. This despite having been referenced in Microsoft's own security bulletin last Tuesday: "Firefox users who are running the Windows Presentation Foundation (WPF) plug-in and do not have it disabled should also apply this security update."
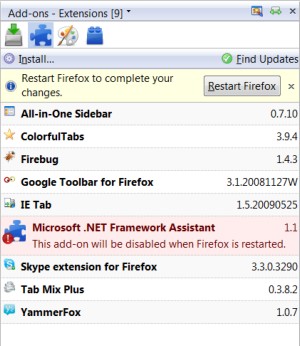
Upon realizing this news, Shaver announced this morning that Mozilla is un-blocking the two extensions [CORRECTION] the .NET Framework Assistant add-on, leaving the WPF plug-in blocked.
Yet that creates an entirely new problem, as Betanews discovered this morning: For the same reasons folks had trouble trying to uninstall these extensions before, they'll have trouble now re-installing them -- though .NET Framework Assistant appears in Firefox's Extensions list, the "Enable" button is greyed out, and the same goes for "Windows Presentation Foundation" in Firefox's Plug-ins list.
In an effort to shed some light on this wild subject, here now are some clarifying facts:
- .NET Framework 3.5 SP1 was not one of the patches presented by Microsoft last Tuesday. When users noticed the two Firefox extensions for the first time this week, it was probably because they ended up installing SP1 at the same time they installed the critical and important Patch Tuesday updates. One of those updates was the Microsoft patch that temporarily disables the extensions' functionality.
- ClickOnce functionality was not the subject of the vulnerability in question. ClickOnce is Microsoft's now extremely ironic brand name for a technology designed to enable .NET applications to update themselves over the Web, a process which requires elevated privilege since installed code is being replaced. While the possibility that .NET code could find itself running with elevated privileges as a result of the ClickOnce problem, the attack vector in question here involves something quite different -- a broad level of possible attack vector that's thus far unexploited (it takes some intelligence), for which .NET Framework was only a case-in-point.
- It's not the extensions that are vulnerable in this instance, but rather the .NET Framework functionality which they enable through the browser.
- Microsoft was not silent about having released its Firefox extensions. In fact, its engineers were quite proud of them, although few independent sources bothered to cover their existence until they became an annoyance (and we're guilty as charged here too). Granted, the world doesn't flock to Scott Hanselman's blog, though engineers can only do so much to tout their efforts. What Microsoft had neglected to do, in hindsight, was provide users with a way to opt out of changing their Firefox settings, or to uninstall these extensions once they appeared there. This has now morphed into a new problem: the lack of any direct ability to re-enable the plug-ins once they've been turned off. Betanews is still experimenting with finding a way to do this (it does not involve editing
about:config, unfortunately), and we'll report it to you once we find it.
During a July presentation at the Black Hat conference by security engineers at Hustle Labs, a Microsoft mechanism called XBAP was used as a case-in-point for a demonstration of a much larger problem: the likelihood of vulnerabilities whenever interoperable code components use so-called variant data types to exchange information. Soon afterward, Microsoft began addressing the possibility of an exploit using an attack vector they feared could be inspired by the Hustle Labs demo.
XBAP is a facilitator for XAML, the XML-based layout language that substitutes for HTML for building Web apps. Microsoft began rolling out XBAP in August 2008, with Service Pack 1 to .NET Framework 3.5. Responding at the time to criticism that the company tends to release Web-based functionality for Internet Explorer only, it produced a ".NET Framework Assistant" add-on to Firefox as well, along with a plug-in that enabled XBAP in Firefox.
But neither extension gave Firefox users an option not for uninstallation. So when it was revealed that .NET's "ClickOnce" technology was potentially vulnerable, Firefox users were compelled to uninstall it manually. When users learned last weekend that Mozilla was blocking these add-ons, some bloggers assumed it was because of the ClickOnce matter, and reported it as such; ClickOnce is actually unrelated here.
Now, the problem going forward could be a number of Firefox users whose browsers are in need of some repair.
5:35 pm EDT October 19, 2009 · Responding to our story from earlier this morning, Mozilla Vice President for Engineering Mike Shaver told Betanews that this morning's unblocking action freed just the .NET Framework Assistant add-on for Firefox, not the Windows Presentation Foundation plug-in. It is Mozilla's belief, Shaver said, that this plug-in may still expose Firefox users to the principal vulnerability addressed in last Tuesday's Microsoft patch, as long as that plug-in remains enabled.
"We were told by Microsoft that the [.NET Assistant] add-on was vulnerable (and in fact at one point that the WPF plug-in was not, but we corrected that in conversation), and waited for confirmation from them that it wasn't before unblocking it," Shaver told Betanews. "We were not correcting ourselves; we were updating based on a Microsoft correction."
