Microsoft security report points to downtrend in malware
There's fewer reports of malware in the wild for the entire industry, Microsoft said this morning -- an indication, it says, that the security field is getting smarter. But once again, do undisclosed vulnerabilities simply not count?
In a more circumspect report than those the company published previously, Microsoft is saying today that the general trend toward malware distribution worldwide is continuing on a decline, and that Microsoft may be contributing to that decline through a reduction in Windows-targeted malware by more than one-third.
Once again, however, the company is basing its statistics on disclosures of vulnerabilities, often comparing them to disclosures for the rest of the industry. Non-Windows disclosures may have risen for any number of reasons, including possibly better vigilance among Linux and Mac OS users and supporters. Of course, it's difficult if not impossible to measure the effects of non-disclosed vulnerabilities; but on the other hand, some troubles are demonstrably more malicious than others.
That said, authors of the latest Microsoft Security Intelligence Report released yesterday are saying that the total number of reported vulnerabilities reported in all software (not just Microsoft) declined in the first half of 2008 by about 4% from the previous sampling period in the second half of 2007, and down 19% from the first half of 2007. However, judging from the breakdown of those reports, the percentage of reports with high severity ratings rose by (if one interprets the graph by eyeball) about 5%.
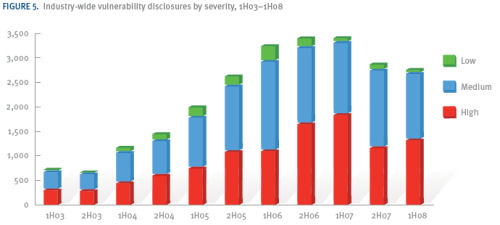
Microsoft's overall contribution to the number of vulnerability reports continues to trend down, states the MSIR, from nearly 10% of all cases during the second half of 2003 to less than 3% in the last six months.
What these numbers mask is the impact that some flaws may have on everyday users, compared against other flaws. On the one hand, the architecture behind last July's extremely critical DNS flaw had been publicly known for years. The formal report of the flaw itself, however, may have been counted as just one vulnerability among many for the first half of the year. Yet the actual impact of the flaw in this case was very minimal, since it did not appear to have been widely exploited to any great degree prior to the efforts of companies including Microsoft, working in conjunction with security researcher Dan Kaminsky.
Thus what might otherwise given someone leverage to cripple the entire Internet actually ended up a blip on the radar.
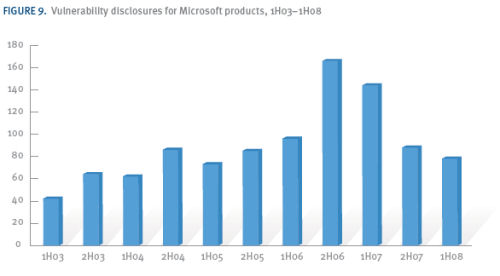
Today's MSIR report also comes clean on a point that was masked over at this time last year: Reports of vulnerabilities in Microsoft products in general rose very sharply during the second half of 2006 -- coincidentally, the time of Vista's volume license release -- only to begin a decline to about half as many today. But last year, the company was touting its relative integrity as much higher, on the basis of very few reports of holes in Windows XP and Vista, versus other operating systems.
Viewpoint depends on where you stand; and in that case, the company was apparently excluding the reality that the attack vectors have spread in such a way that malware targets applications rather than the OS specifically. Third-party software is becoming the attack vector of choice, and Microsoft was clearer about that point in today's report. During the first half of the year, it states, 42.3% of reports of browser-based exploits specifically targeted Windows XP, with the remainder targeting third-party software (conceivably Adobe Flash may be included in that bunch). By comparison, only 5.7% of reports of browser-based exploits on systems running Vista were for malware that actually targeted Vista specifically.
Again, this is not to say less malware targets Vista -- that would be an inaccurate conclusion, though Microsoft leaves the door open for those who wish to draw that conclusion. Rather, there are fewer reports of such incidents, which is an indication that attempts at exploiting Vista-based browsers are failing.
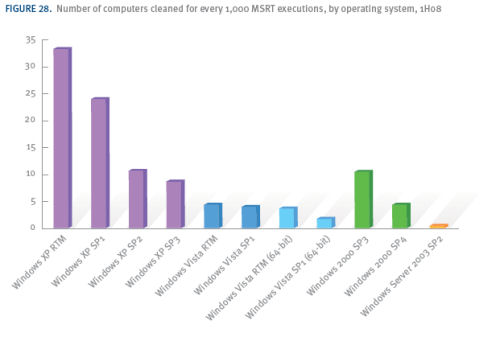
This season's report refrained from drawing blanket comparisons of Windows' relative safety compared to Mac OS or Linux, a subject which got Microsoft into hot water last year. It does compare versions of Windows to one another, with each successive version appearing to have fewer reports. However, while Vista SP1 seems to have slightly fewer reports than the original Vista RTM version for the first half of the year, SP1 only began distribution in late March.
In just the United States, the single most effective family of worms in the wild was the malicious IE-targeting Trojan Win32/Zlob, according to the MSIR report, with 5,427,360 infected computers -- more than double the amount of the #2 worm, adware Trojan Win32/Vundo.
