Shields down -- IPv6 is not ready for attack
Get ready folks for the Information Superhighway of the future, one with 2128 lanes.
It's World IPv6 Day, a day when we're all supposed to check our readiness for the next version of IP, or Internet Protocol, the Internet Layer protocol of the Internet and almost all networks these days. IPv6, of course, is an old story, since it was long ago that we recognized the address space of IPv4 would run out, and we're almost there. The IPv6 address space, as I have written before, is so large that we may just take it with us to the first few planets we colonize.
But real world adoption of IPv6 has been, to put it kindly, really, really slow. IPv6 support first showed up in the Linux kernel in 1996. Other UNIces shipped it over the next several years. Windows end users got it in 2002 and Macs in 2003 in Panther. Many of these systems not only provided IPv6 support, but turned it on by default.
Of course, you need some place to communicate with. There are many popular websites with at least some support for IPv6. Google has been relatively aggressive in this regard. Many other sites and services are not. You also need Internet service that routes IPv6 traffic. Higher-end business services support it. but very few consumer ISPs do.
As a result of this, and in spite of years of advocacy and government mandates, IPv6 traffic remains a small percentage of overall traffic, according to a recent study by Arbor Networks. They looked at six large service providers in North America and Europe over six months. All IPv6 traffic typically ran in the neighborhood of 0.15 percent with brief peaks as high as 0.3 percent. The large majority of this traffic is tunneled traffic, using transition protocols like 6to4 or Teredo, yet tunneled traffic never exceeded 0.05 percent of overall traffic and usually constituted much less.
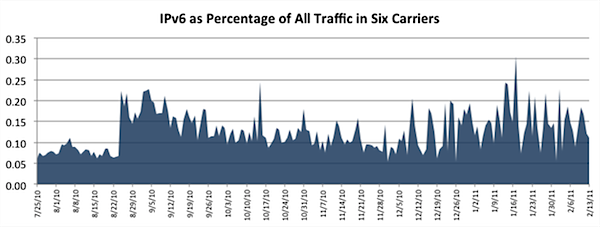
Image courtesy of Arbor Networks
So IPv6 is a failure so far. But we know what has to be done, so World IPv6 Day is the next in a series of advocacy events to get people excited about IPv6 and testing their products. The point of this day is interoperability. But I'm a security guy, so I always look at these things from a security standpoint. And the most encouraging thing I see about IPv6 from a security standpoint is that it's really hard to find in the real world.
Here's an interesting quote from the Arbor report:
P2P continues to dominate at more than 60% of all IPv6 traffic. ... Unlike IPv4 P2P, the data suggests most IPv6 P2P application makes little effort to encrypt or use randomized ports. This IPv6 P2P behavior may correspond to the relative lack of IPv6 capable firewall and traffic management solutions. At a distant second and third, Web and SSH both average 4.6% of IPv6 traffic.
The bottom line from observations like this is that IPv6 is not even in its infancy in terms of development. It's more like a fetus. And while clearly a lot of thought and experience went into the security design of IPv6, nothing is secure by design. It's a rock-solid certainty, as we gain real-world experience with IPv6 and malicious actors find incentives to research and attack it, that we will find serious security problems with it. We have virtually none of that experience today, and World IPv6 Day won't add to it, because it's only looking for interoperability.
Ron Meyran, director of Security Marketing at Radware, pitched this idea to me, and he's right on. The transition period to IPv6, Meyran says, will be especially dangerous because there's no way the security products will be mature enough to handle the environment. Another good example of this is the transition period. Everyone has always known that the transition period would not involve throwing a big switch and moving from all IPv4 to IPv6. There are tunneling schemes, known as Teredo and 6to4, for allowing users to mix and match IPv4 and IPv6 networks and services. Unfortunately, these add complexity to the mix, and with complexity you always get security problems.
Undoubtedly major ISPs, sites and enterprises appreciate this catch-22 and this explains a lot of the reticence to put more than a toe in the IPv6 waters.
An an example of the unintended consequences, a few months ago John Levine pointed out how the vast network assignments that come with IPv6 service will make IP blacklisting for purposes of spam blocking nearly impossible. Meyran agrees with Levine.
The final great irony from Meyran about IPv6 is that there are very few IPv6 attack tools. Some people would think this is a good thing, but in fact it makes IPv6 less secure because legitimate researchers and customers can't determine what the vulnerabilities are.
Interoperability is obviously important, but in the case of IPv6 it's far from adequate. We face the mother of all chicken-and-egg problems here: Customers won't, and shouldn't, adopt IPv6 until it's mature enough to be considered secure. And it won't get secure if nobody uses it. Not a pretty picture.
 Larry Seltzer is a freelance writer and consultant, dealing mostly with security matters. He has written recently for Infoworld, eWEEK, Dr. Dobb's Journal, and is a Contributing Editor at PC Magazine and author of their Security Watch blog. He has also written for Symantec Authentication (formerly VeriSign) and Lumension's Intelligent Whitelisting site.
Larry Seltzer is a freelance writer and consultant, dealing mostly with security matters. He has written recently for Infoworld, eWEEK, Dr. Dobb's Journal, and is a Contributing Editor at PC Magazine and author of their Security Watch blog. He has also written for Symantec Authentication (formerly VeriSign) and Lumension's Intelligent Whitelisting site.
Editor's Note: This story was originally posted June 7, 2011 at 12:52 p.m. EDT.
