The oldest trick in the book, literally, defeats UAC in Windows 7
Though the fellows sounding the warning today are the best in the business, it didn't take a lot of know-how to develop a proof-of-concept that the new User Access Control panel can be disabled by VBScript.
Windows 7 is still in the public beta process, and will be for some months to come. The purpose of true beta testing is to isolate and identify serious problems (we should know). So it's to any researcher's credit that a potentially threatening problem be brought into the open prior to Microsoft finalizing the code for everyday use.
That said, it's an little embarrassing to discover that a dumbfoundingly simple method for forcing Windows to accept keypresses from a script as though they'd been pressed by a human being, is the focus of a proof-of-concept macro capable of disengaging User Account Control in Windows 7. The macro was published this morning by developer Rafael Rivera, and then kicked into the public spotlight by expert blogger Long Zheng.
There almost no way to talk about this bypass methodology without divulging how to use it. I know this personally more than perhaps anyone alive: In researching a book I wrote 18 years ago, I ended up discovering its potential use in malware perhaps before anyone else. It has to do with a method introduced in Visual Basic and carried forth in VBScript called SendKeys; and already, half of my readers know what I'm talking about. By sending keystrokes to Windows, any script using this method does not have to be authenticated, because Windows always thinks any keystroke a program receives is being sent by a human user.
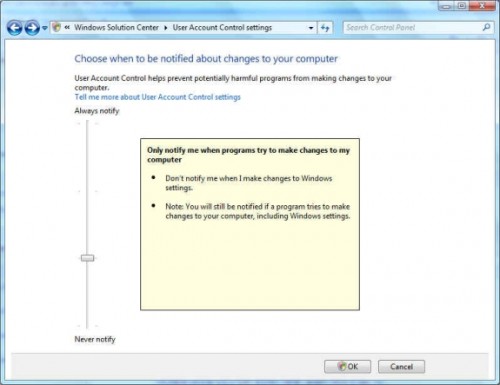
In Windows 7, the new User Account Control slider dialog that appears in the system's new Action Center enables users to turn off the "nags" that bothered them so much in Windows Vista. In so doing, however, they disengage one of the system's key security features, though this slider does give users the freedom to do just that, and we've been promised that on business systems, administrators will be given some form of group policy control that can shut off access to this slider to designated users.
Indeed, the SendKeys method is capable of sending up and down keypresses to this panel, and can even send the keypresses necessary to make the panel appear. Rivera warns that real malware could conceivably be used to not only force UAC to turn off, but then to reboot Windows and run a malicious package with full privileges. (His PoC, however, does not do that.)
Long Zheng has been one of the many developers and experts and others -- myself included -- who have warned Microsoft about the potential of leaving open any kind of hole in the Secure Desktop, which is what Vista relies upon to make UAC work. Secure Desktop shuts off all system access from the outside world -- including from SendKeys -- temporarily, and then dims the screen before UAC asks the user whether a process can be allowed to continue. This sometimes annoying and bothersome methodology has been key to Vista's reduced incidents of cracks and vulnerabilities.
As Zheng writes this morning, "There is a simple fix to this problem Microsoft can implement without sacrificing any of the benefits the new UAC model provides, and that is to force a UAC prompt in Secure Desktop mode whenever UAC is changed, regardless of its current state. This is not a fool-proof solution (users can still inadvertently click 'yes') but a simple one I would encourage Microsoft to implement seeing how they're on a tight deadline to ship this. Having UAC on at the policy as it is currently implemented in Windows 7 is as good as not having it on at all."
A true story: In 1993, a film documentary team with the German TV network ZDF spent several weeks filming a team of self-proclaimed hackers from the cultural underground. Without turning any of them in to authorities and while keeping their identities secret, the crew filmed these guys as they demonstrated code for capturing key sequences from unsuspecting users who had been given special online programs for logging into their bank accounts (this was before the advent of the Web).
When asked how long it took to discover the methods for capturing and repeating key sequences, one of the group's leaders responded -- as I recall, through the English translation -- something to the effect of, "We didn't have to discover it." Then he held up a copy of my book and said, "It's idiots like these guys who'll tell us how to do it for free."
